Thousands of Magento Stores Infected by GuruIncSite Malware
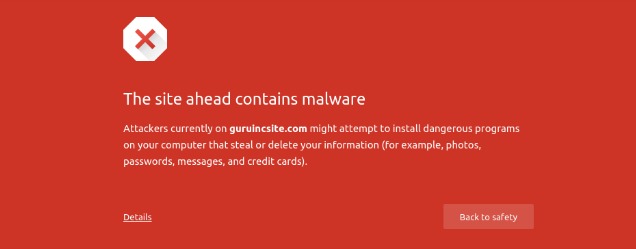
Over the weekend, a large number of Magento sites have been hit by a massive javascript injection hack referred to as the GuruInc malware. Allegedly thousands of stores are already infected. The malware exploits a vulnerability in Magento or a 3rd party extension to inject a piece of javascript malware into the Magento database, which then infects any visitor to the site. Google has currently blacklisted more than 8,000 domains affected by the hack.
Online security company Sucuri Labs said the attack involves the injection of malicious scripts through iframes from the domain guruincsite.com. Both an obfuscated and non-obfuscated version of the infection has been reported.
The malicious code is usually added in the Footer - Miscellaneous Scripts section or in a CMS page of the Magento installation.
Sucuri is investigating the spread of Guruincsite and suspect "it was some vulnerability in Magento or one of the third-party extensions that allowed it to infect thousands of sites within a short time." However, the actual attack vector is yet to be discovered.
Researchers from Malwarebytes say guruincsite shares several similarities with a campaign using the Neutrino Exploit Kit. The "neitrino" cyberattack campaign uses the same attack on the server side that Sucuri noticed, but instead compromises domains client side via web exploits. Websites compromised through a Flash exploit are harvested for financial data and also become slaves to a botnet system.
Is my store infected?
Check the page source of your Magento home page and look for code similar to the below snippets. You can also scan your site for free using the following tools:
https://www.magereport.com
https://sitecheck.sucuri.net
These tools will detect the GuruInc exploit as well as other malware and known vulnerabilities.
Mitigation
To remove the guruincsite malware from an infected Magento site, you should follow these steps:
- Navigate to System > Configuration > Design > Footer > Miscellaneous HTML and remove the malicious code there. The hack can be identified by the presence of the code function LCWEHH(XHFER1)[...]. If you prefer to edit the database directly, look for the design/footer/absolute_footer entry of the core_config_data table.

- Navigate to CMS > Pages > Home > Content and delete the malicious code in the <script> tag (selected on the screenshot):

- Delete any unknown admin users from System > Permissions > Users.
- Finally, make sure that you are running the latest version of Magento and that all security patches have been applied.
As a hacker may have gained access to your database credentials, we also recommend that you change the database user and password as well as the password of all Magento admin users.
When you have completed the above steps, please re-run a vulnerability check to confirm your site is clean.
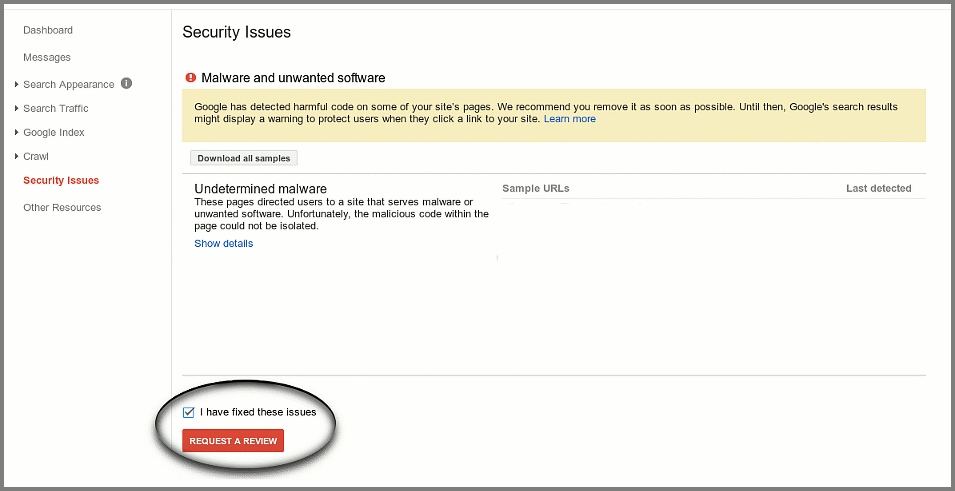
Re-submission to Google
If Google has blacklisted your site, make sure to log into Google Webmaster Tools and from the Security tab confirm that the malware has been removed from the site. The warning should disappear after a couple of hours.